eBay Impersonated in Gift Card Invoice Attack
Gift card fraud has been a staple of cybercriminals for years. Converting gift cards into cash is quick and easy, and attackers are rarely pursued for conducting these scams. Once the attacker has the gift cards, they can use them to purchase items or sell them at a discounted...
January 21, 2021

Gift card fraud has been a staple of cybercriminals for years. Converting gift cards into cash is quick and easy, and attackers are rarely pursued for conducting these scams. Once the attacker has the gift cards, they can use them to purchase items or sell them at a discounted rate on the web.
This attack features a unique attempt to conduct gift card fraud by impersonating a used car sale through eBay. In this attack, attackers utilize a lookalike domain to impersonate eBay in an attempt to trick users into sending overpayment in gift cards.
Summary of Attack Target
Platform: Office 365
Bypassed Email Security: Proofpoint
Victims: Employees
Payload: Text/Attachment
Technique: Impersonation
Overview of eBay Gift Card Invoice Attack
This attack ostensibly originates from eBay’s motor department with the sender "ebay@vpp-motors-department-inc.com" and display name “eBay motors”. The message thanks the recipient by name and states that their invoice is attached with the necessary information to complete the transaction. The aforementioned invoice is attached as a PDF to the email.
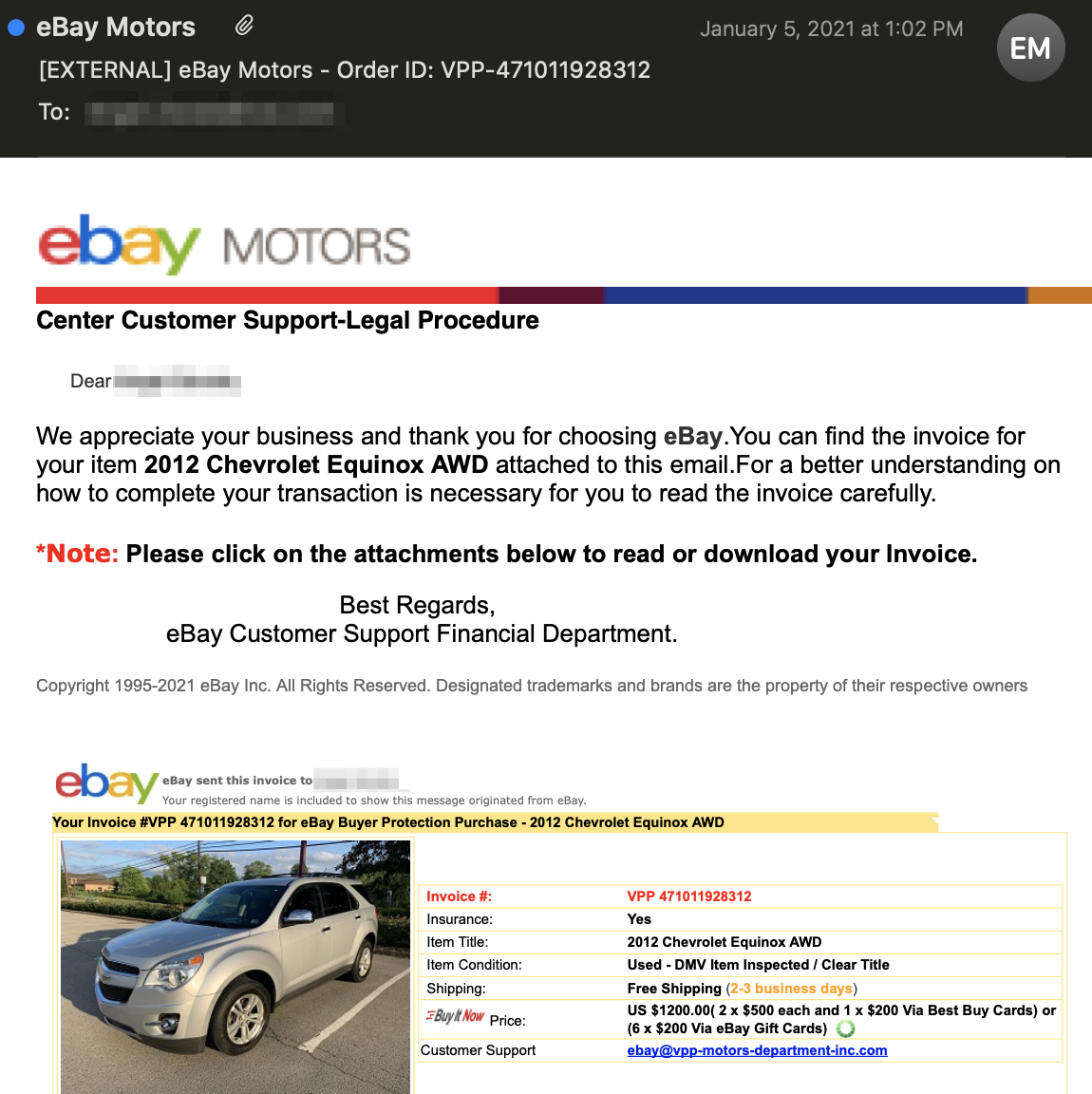
The payload for this attack is neither a link nor a malware attachment. Like most gift card fraud, it's entirely text-based. The body text and PDF attachment contain no malicious links or payload, instead relying on the recipient to read and engage with the attacker. The attached invoice states that their car purchase was accepted and that they must send payment in the form of specific eBay or Best Buy gift cards.
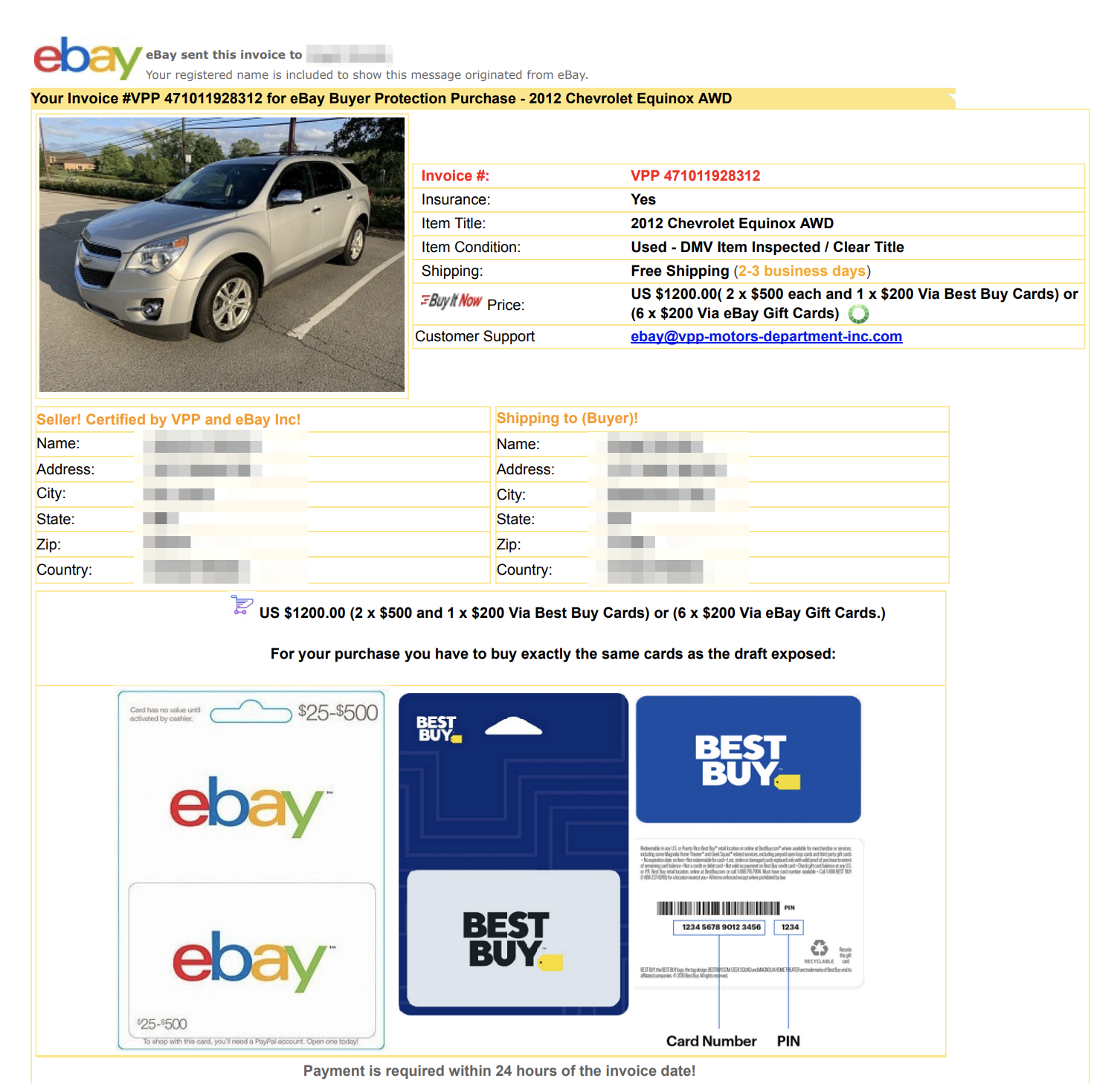
Additionally, the invoice attachment contains instructions on where to go to purchase gift cards and the proper steps to send over the codes in order to “verify” payment.

If the recipients do not realize that this transaction is fraudulent and unrequited, they may provide attackers with the gift card information and be liable for significant financial loss.
Why the eBay Gift Card Attack is Effective
In this attack, the attacker meticulously impersonated eBay in the message itself and the attachment. The sender's email address and domain are ‘eBay’ and ‘vpp-motors-department-inc.com’, where VPP is eBay’s ‘Vehicle Protection Program’. Furthermore, the body and attachment consistently emphasize the message originates from eBay and is doctored to appear as a legitimate invoice from eBay.
While gift card fraud attacks normally cast a wide net for victims, this particular type of attack is specifically tailored to the recipient. The body text of the email is addressed to the target and all references to shipping and other typical invoice information mention the victim by name. Furthermore, the shipping information for the vehicle appears to be a legitimate address meaning that the attacker has conducted thorough research before sending out this attack to their potential victims. If a user was expecting to receive instructions on how to pay for this car, they could be easily tricked into doing so via gift cards.
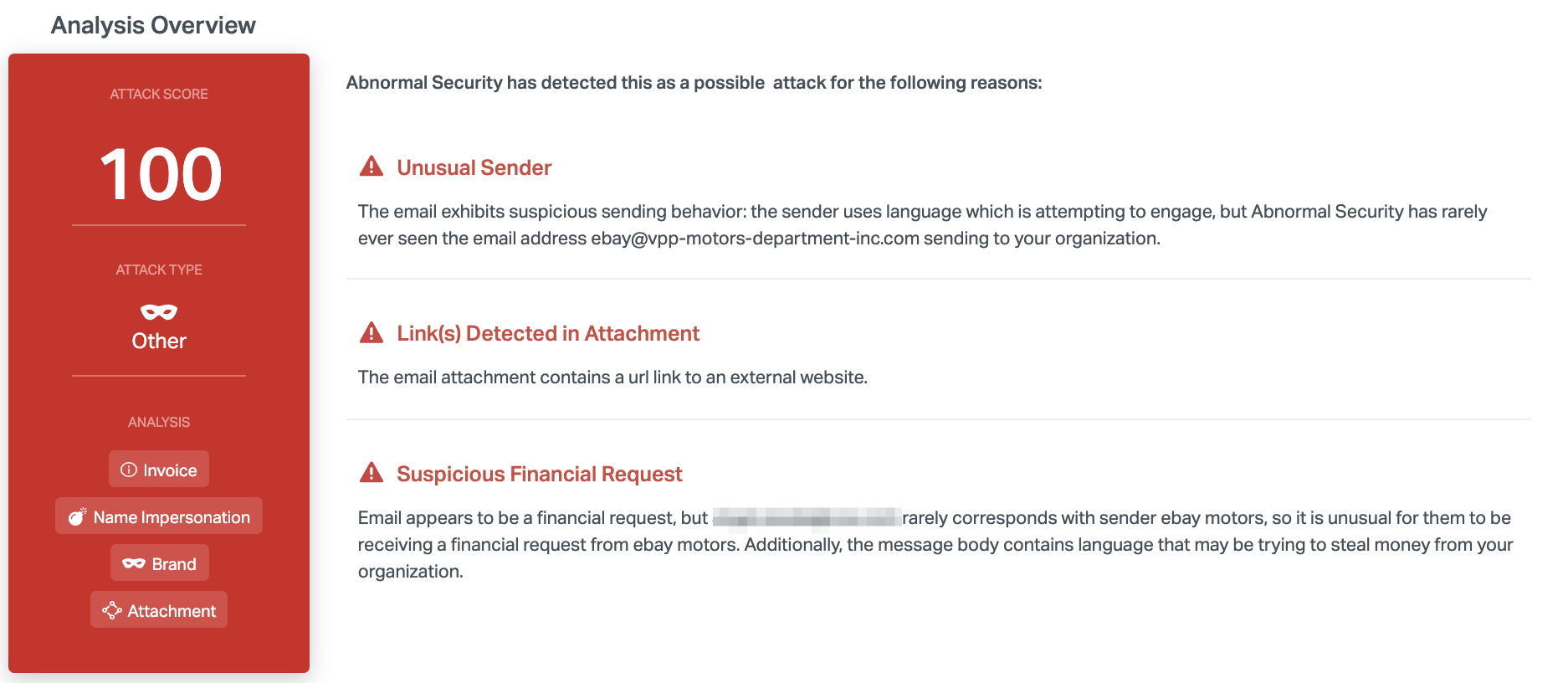
Abnormal detected this email due to a variety of suspicious indicators, including the unusual sender address and the suspicious financial request. The brand impersonation and the gift card content are both key parts of the attack, and understanding the intent behind the message is critical to stopping it before targets become victims.
To learn more about how Abnormal uses content and identity to stop advanced attacks, see a demo today.
Related Posts
Get the Latest Email Security Insights
Subscribe to our newsletter to receive updates on the latest attacks and new trends in the email threat landscape.

