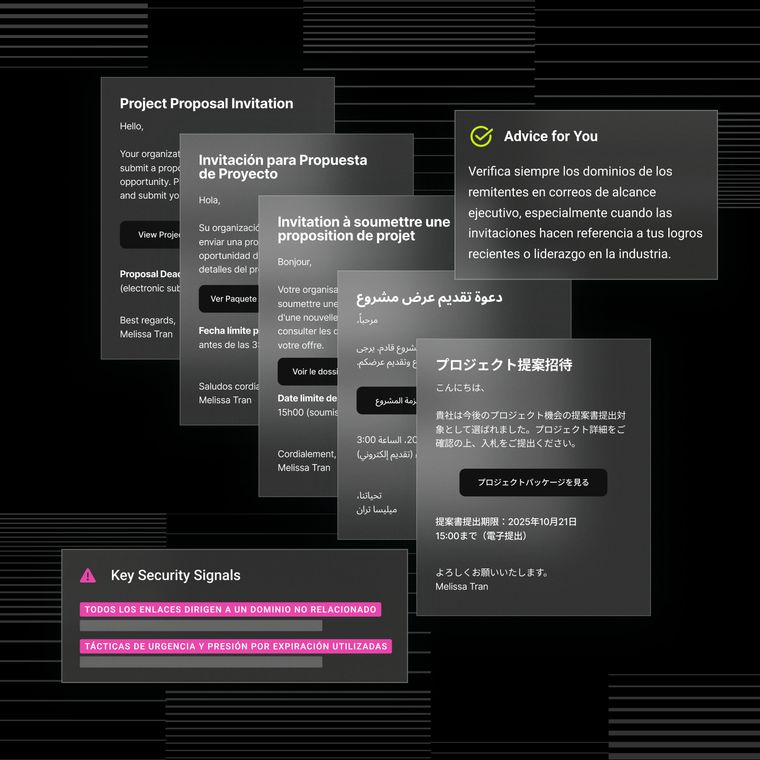
New SIEM Integrations Improve Incident Response Capabilities and Streamline Workflows
Abnormal is focused on our customers, which is why we’re continually updating our product based on customer feedback. Our newest platform capabilities help customers maximize existing security investments with several integrations that will allow security operation centers (SOCs) to better respond to security events and align with internal workflows.
Dallas Young, Vineet Edupuganti
November 5, 2021

Abnormal is focused on our customers, which is why we’re continually updating our product based on customer feedback. Our newest platform capabilities help customers maximize existing security investments with several integrations that will allow security operation centers (SOCs) to better respond to security events and align with internal workflows. In doing so, they can improve overall security posture and provide complete protection to their organizations and employees.
Improved Security Monitoring and Visibility
We are excited to introduce new integrations with security information and event management (SIEM) solutions, including Microsoft Azure Sentinel, Sumo Logic, and IBM QRadar. Similar to our existing Splunk integration, these integrations are quick and easy to set up, with integration completed in less than ten minutes. Once connected, customers can ingest Abnormal event logs derived from inbound email threats and account takeover (ATO) cases into their SIEM tool, which can optionally be configured for alerting and other downstream workflows.

*Abnormal has over 30+ data fields that can be exported and additional SIEM & SOAR providers supported. Learn more here.
Benefits of Integrating Abnormal with Your SIEM
These integrations extend Abnormal’s powerful detection platform to integrate with the broader security ecosystem, thereby improving security posture and enhancing detection and response capabilities. Customers can leverage their existing tools to boost analyst efficiency and ensure comprehensive security visibility and coverage, ultimately reducing the impact of security events.
Customers can also perform threat analysis by cross-correlating alerts originating from various security tools, building out reporting and dashboarding systems that include Abnormal data, and enriching their centralized logs, which are useful for compliance and audit purposes. Already, our customers have seen success correlating data from their endpoint security solutions such as Crowdstrike Falcon with Abnormal.

Functional Use Cases
There are over thirty data fields that can be exported to your preferred SIEM. Some popular use cases we’ve observed with Abnormal’s rich data include:
Threat analysis. Several customers use threat data exported from Abnormal’s detection platform alongside logs generated by other security products to identify attack patterns. Additionally, security analysts can correlate different events to better understand specific attacks and drive follow-up activities, including contacting end users, updating block lists, or providing training to employees.
Dashboarding and reporting. Many customers will use their SIEM as a “single pane of glass” across their security products. Based on Abnormal’s logs for email threats and account takeover (ATO) cases, customers can build executive dashboards or reports for the security team.
Alerting and ticketing workflows. Abnormal customers can trigger custom email notifications or generate tickets, such as with ServiceNow from the SIEM to align with the SOC’s workflow.
Audit and compliance. Customers with log retention requirements, especially those in regulated industries like finance or healthcare, can import all security events, including Abnormal, into their SIEM for centralized and unified storage.
These partner integrations represent a more significant tie-in between Abnormal and the rest of the security ecosystem. By strengthening your organization’s security posture and workflows, these integrations enable you to gain increased leverage on existing investments in the tools you already operate.
Over time, we aim to continually work with our customers so they can focus their efforts on the highest priority security events, as opposed to manual operations. These themes will guide us as we continue to expand our suite of integrations going forward.
To learn how Abnormal can improve email incident response capabilities and streamline workflows for your organization, request a demo today.
Related Posts
Get the Latest Email Security Insights
Subscribe to our newsletter to receive updates on the latest attacks and new trends in the email threat landscape.