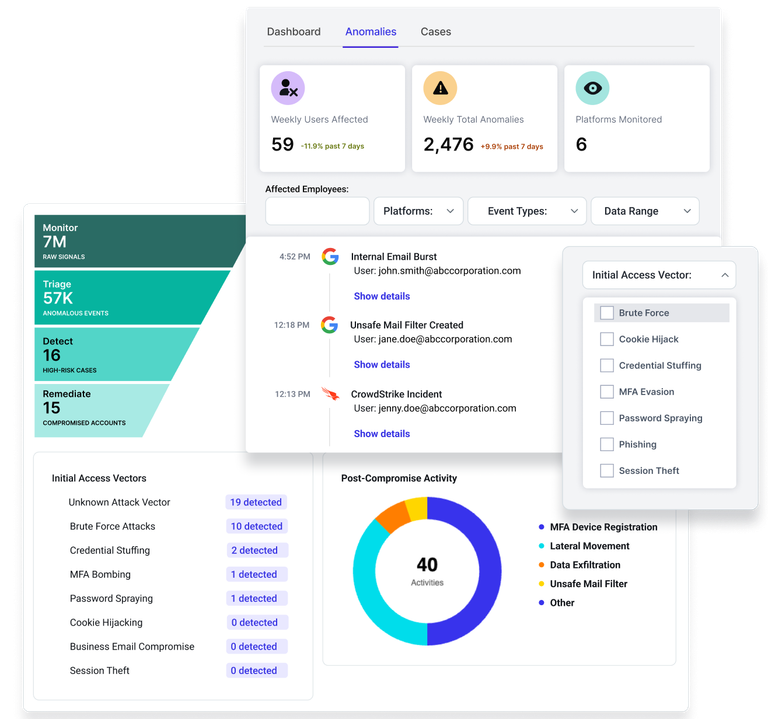
Account Takeover now includes new tabs that help security teams better understand how Account Takeover activity is detected and how it develops across the environment.
What’s new:
-
Account Takeover Dashboard shows how identity, email, and SaaS signals are monitored, flagged as anomalies, and correlated into confirmed ATO cases, with aggregated trends and direct links into related cases.
-
Anomaly Log provides a searchable view of suspicious identity and email activity evaluated as part of ATO detection, even when no case is created.
-
Attack Vector Classifications identifies the initial access vector for each Account Takeover case and surfaces aggregated patterns to highlight common attack methods.
These updates add visibility into account takeover activity from early signals through detected cases, helping teams review trends, prioritize response, and better understand how attackers are gaining access.