Abnormal Improves Attack Detection Efficacy Against Hidden Payloads by 5%
Abnormal’s relentless pursuit of innovation significantly improves the detection efficacy of hidden payloads in emails by an additional 5%.
January 7, 2022

Enhanced Hidden Payload Analysis and Detection Detection Accuracy
While our detection capabilities have always been best-in-class, attackers constantly evolve their tactics. Approximately 69% of advanced attacks are payload-based, targeting our customers. A payload-based email attack contains a malicious attachment, URL, or combination of both. In order to relentlessly improve our product and stay ahead of the attacks, our engineering team identified trends in customer cases, which was accomplished by grouping similar behaviors and observations together.
By improving our ability to analyze previously hidden payloads, our detection engines can more precisely identify malicious payload-based attacks and give our customers even better protection against such attacks. The Abnormal engineering and first responder teams minimized our customer false negatives rate by 5%, improving our ability to analyze hidden payloads.
New Hidden Payload Detection Methodologies
In this release, we shipped improvements to address these three classes of hard-to-analyze payloads:
- Wrapped URLs. A wrapped URL is essentially a URL embedded inside another URL. Security vendors often utilize URL wrapping to track clicks on links and optionally redirect to a block page if they are able to detect the content is bad at the time of click, oftentimes this makes it difficult to analyze the original URL sent in the email when downstream from another security solution. We improved our ability to retrieve the original URL or domain when we detect that a URL is wrapped without clicking the link. This allows us to determine whether or not the original URL is malicious more effectively.
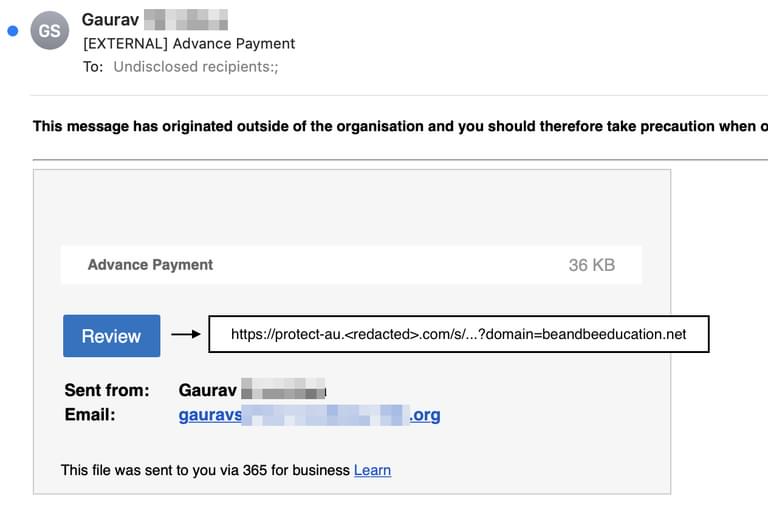
Wrapped URL example to redirect from one URL [protect-au.com] to another URL [beandbeeducation.net] - Encoded HTML attachments. We added enhanced detection capabilities to detect when an encoded HTML attachment is present in the email. Combined with communication-pattern-based features, this allows us to precisely detect when an email containing an encoded attachment is malicious.
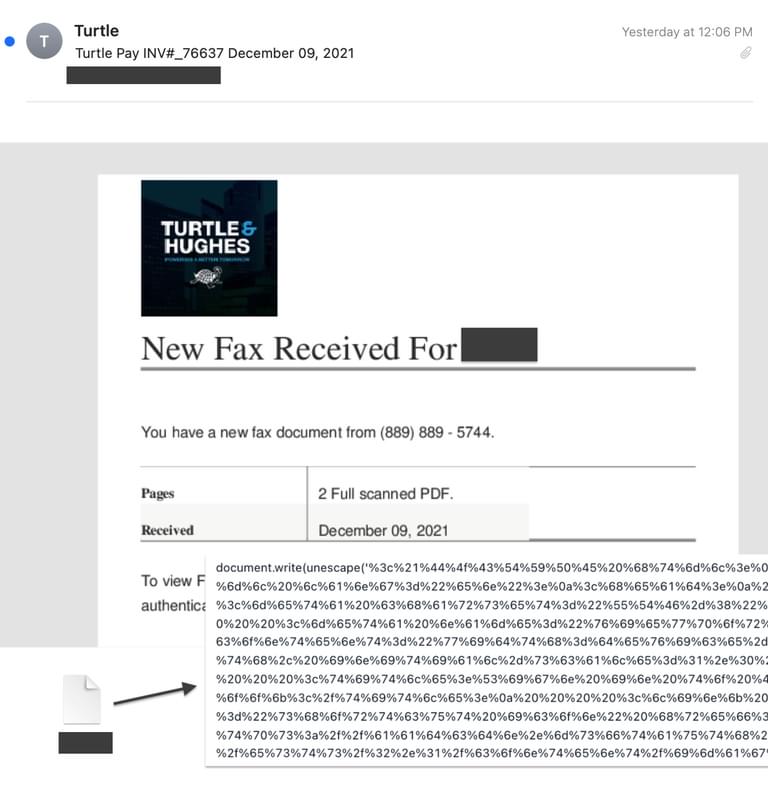
An example of an HTML encoded email with malicious code
Encoded HTML attachments have legitimate business uses, such as instructing a web browser or email application how to interpret the text characters in your HTML or the body of the email to maintain consistent formatting. There is a high chance that you have received an embedded email recently that was probably a phishing attack. The HTML attachment often hosts web pages on the victim’s computer instead of the internet, which is a stealthy method for bad actors to avoid URL reputation checks. - HTML attachments with redirect scripts. When an HTML attachment contains a redirect script, we added features to detect it. Furthermore, combined with user communication-pattern-based features, we can precisely identify when an email with a redirect script is malicious.
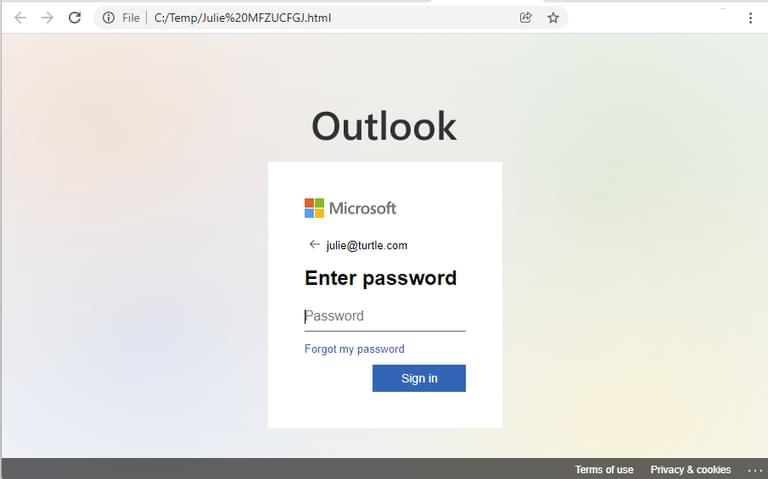
HTML attachment with a redirect script used for credential harvesting
The combined benefits of further increasing the detection efficacy of malicious payloads embedded in email messages by 5% further protects customers against these attacks. This helps IT security teams minimize exposure to threats lurking within mailboxes that could lead to account takeovers, malware infections, intellectual property losses, compliance issues, or even lawsuits over data breaches.
Learn More
Abnormal is committed to constant innovation to improve our detection capabilities, including our expansive machine learning capabilities to help security teams stay ahead of the attackers.
Want to learn more? Request a demo today.
Related Posts
Get the Latest Email Security Insights
Subscribe to our newsletter to receive updates on the latest attacks and new trends in the email threat landscape.


