Executive Email Account Takeovers in the News: Unpacking Midnight Blizzard
A recent nation-state actor attack by the Russian-backed threat group Midnight Blizzard infiltrated Microsoft. Discover how Abnormal can protect you from account takeovers in real time.
March 11, 2024

Key Takeaways
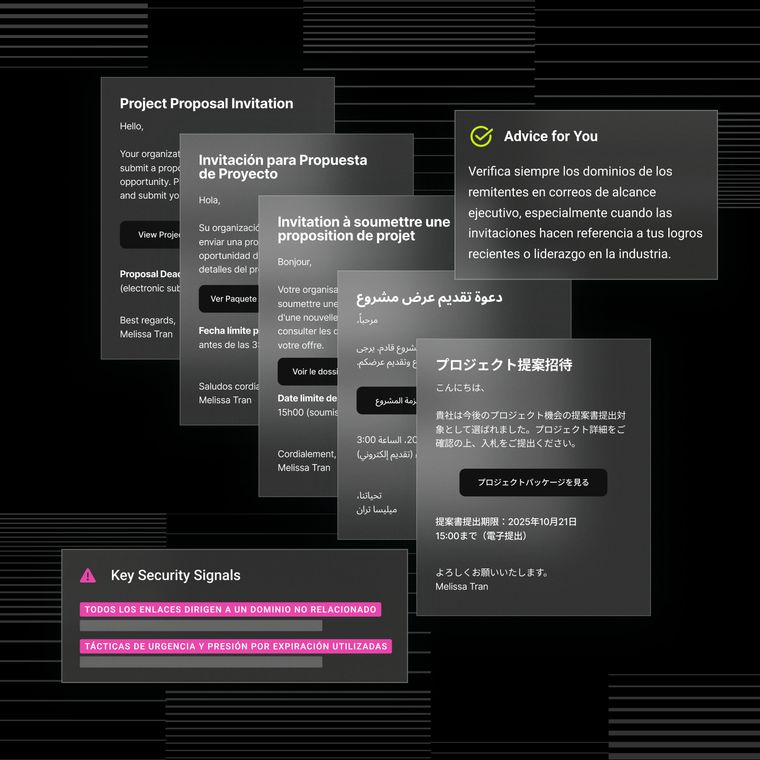
- Midnight Blizzard infiltrated Microsoft's Exchange environment, leading to the compromise of top executives' mailboxes.
- The attackers used password spraying, obfuscation through proxy infrastructure, and exploitation of OAuth applications to gain access and exfiltrate email communications.
- To protect against similar attacks, organizations should enable MFA, actively monitor their cloud email platforms, and consider implementing an AI-powered solution.
Related Posts
Get the Latest Email Security Insights
Subscribe to our newsletter to receive updates on the latest attacks and new trends in the email threat landscape.