ShinyHunters SSO Attacks: How Social Engineering and MFA Abuse Drive Identity Compromise
Learn how ShinyHunters uses hybrid vishing, credential harvesting, and MFA abuse to compromise SSO and pivot into SaaS environments.
February 6, 2026
/
7 min read

A wave of attacks attributed to actors operating under the ShinyHunters banner underscores a critical trend in enterprise security: identity compromise is becoming an increasingly reliable and scalable way for attackers to gain access to cloud environments.
Rather than exploiting software vulnerabilities, these campaigns weaponize something far more difficult to patch: human trust. By combining voice-based social engineering with real-time credential harvesting and MFA manipulation, attackers compromise single sign-on (SSO) environments and pivot into cloud applications for data exfiltration and extortion.
Headlines have focused on the scale and notoriety of breached organizations, but the real lesson for defenders is how easily identity systems not designed for social engineering can be manipulated when attackers synchronize multiple deception vectors.
How the Campaign Works: Hybrid Vishing Meets Real-Time Phishing
What makes this campaign particularly effective—and difficult to stop—is the way attackers blend human manipulation with sophisticated technical infrastructure. Reporting indicates these attacks typically unfold in five coordinated steps:
1. Target Selection and Reconnaissance
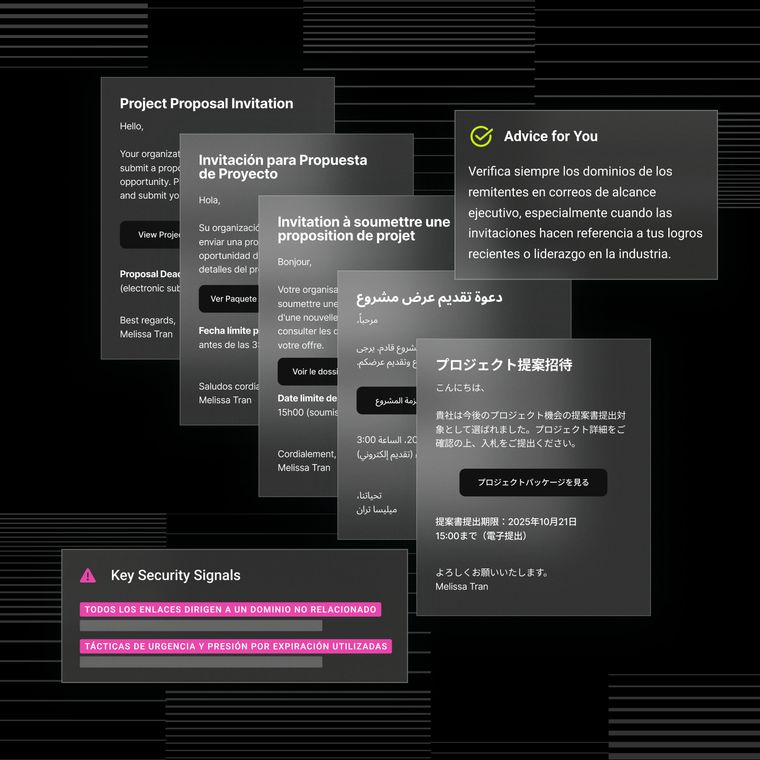
Attackers identify employees within targeted organizations and prepare infrastructure designed to support social engineering attempts. This preparation may include creating phishing pages that replicate legitimate SSO login portals and developing materials used during impersonation attempts.
2. Human-Led Social Engineering (Vishing)
Attackers contact employees directly by phone, often impersonating internal IT or security personnel. They create urgency around account verification, MFA configuration, or login troubleshooting in order to convince targets to follow instructions that appear to be part of legitimate security processes.
3. Live Credential Harvesting
While on the phone, targets are directed to highly convincing, target-branded phishing pages that mimic legitimate SSO login portals (e.g., Okta, Microsoft Entra, Google Identity). These pages are often customized to reflect the target organization's branding, making them difficult to distinguish from legitimate login flows. Attackers capture username, password, and MFA codes in real time.
4. Unauthorized MFA Enrollment and Persistent Access
Using captured credentials and authentication information, attackers enroll their own MFA device or use target-approved MFA prompts to gain access to identity platforms. This enables attackers to maintain access to compromised SSO environments and connected applications.
5. Pivot to SaaS Applications and Data Theft
After gaining access, attackers use compromised accounts to access SaaS applications connected through SSO environments. These applications may contain sensitive business data, internal communications, or customer information that attackers can access, collect, and use to support extortion or data leak activity.
This humans-in-the-loop exploit succeeds because each individual step appears legitimate when viewed in isolation. Authentication events occur through trusted identity providers; SaaS application access comes from valid user accounts. And because the interaction is guided by live social engineering, many technical safeguards are circumvented through user cooperation.
Why Traditional Defenses Fall Short
The success of these campaigns exposes several fundamental limitations in conventional, perimeter‑focused identity and email security approaches that rely on static rules and signatures.
Today's identity and access tools are built on the assumption that MFA challenges and SSO flows will stop automated attacks. But in these campaigns:
Push-based MFA and number matching aren't sufficient when users are deceived into approving challenges while on the phone
Email gateways and secure web filters don't inspect voice channels or live credential capture flows
Network firewalls and proxies don't flag legitimate SSO and SaaS traffic initiated by compromised sessions
Identity logs alone often lack the behavioral context to distinguish normal from malicious access patterns
Many defensive tools are designed to detect malicious infrastructure, suspicious domains, or known phishing templates. In this campaign, attackers frequently use customized infrastructure and legitimate authentication flows, reducing the effectiveness of signature-based detection methods. By the time suspicious behavior becomes visible through log‑centric, infrastructure‑focused monitoring alone, sensitive data may already be exposed.
What This Campaign Reveals About the Modern Threat Landscape
The ShinyHunters activity spotlights a shift that has been accelerating across the threat ecosystem. Because identity platforms centralize authentication across enterprise applications, compromised SSO credentials can grant attackers trusted access across entire SaaS environments.
This changes the economics of cybercrime. Instead of developing malware or exploiting vulnerabilities across multiple systems, attackers can focus on compromising a single identity workflow and use that access to expand their reach. The rise of SaaS adoption and remote work has only increased the value of identity compromise as an entry point.
Another notable aspect of this campaign is the growing use of hybrid social engineering. Attackers are no longer relying on email alone. Voice calls, messaging platforms, and real-time interaction allow them to manipulate trust and overcome defenses that were never designed to be resilient against human-directed deception.
What Defenders Should Prioritize
For security teams, this campaign emphasizes the importance of understanding human behavior as a core component of identity security. While there is no single control that stops attacks like these, organizations can significantly reduce risk by strengthening identity-centric defenses and tightening high-risk workflows.
Move Beyond Password + MFA as a Silver Bullet
MFA remains essential—but only if it's resilient to manipulation. Push notifications and one-time passwords (OTPs) can be socially engineered. Stronger controls, such as phishing-resistant FIDO2 keys, passkeys, or biometrics, raise the bar by design.
Profile Normal Behavior, Not Just Credentials
When attackers successfully capture credentials and MFA responses, they gain access that appears legitimate from a purely identity-centric viewpoint. Continuous monitoring that understands typical login locations, device profiles, and access patterns can spot anomalies that signature-based tools miss. Behavioral signals—such as a verified employee logging in from an unusual region or accessing applications outside their normal role—are early indicators of compromise.
Harden Identity Workflows
Review and tighten manual processes around MFA enrollment, password resets, and privileged access changes. High-risk actions shouldn't be performed based solely on email or voice requests. Introduce additional verification requirements for these critical identity operations.
Elevate User Awareness and Training
Technical controls matter, but so does user judgment. Education on modern social engineering—especially voice-based and real-time deception tactics—must complement phishing simulations. Users need to know how attackers sound, not just what links they click.
Expand Visibility Beyond Authentication
Many breaches escalate not during the initial login, but during the attacker's exploration of SaaS environments and data repositories. Organizations need visibility into what happens after authentication, including access to applications or datasets outside a user's normal role, sudden increases in data access or export activity, and login activity that occurs immediately after high-risk identity workflow changes.
Why Behavioral Context Is Essential
Campaigns like this demonstrate why authentication alone cannot serve as a reliable indicator of trust. In an environment where attackers can mimic trusted systems and social interactions, defenders need tools that understand intent and behavior, not just signatures and static rules.
At Abnormal, we've long championed behavioral AI and identity-centric visibility because today's threats don't stop at the inbox. We consistently observe that the most damaging attacks rarely rely on malware or infrastructure-based indicators. Instead, they rely on carefully crafted social engineering designed to obtain legitimate access.
Our approach focuses on understanding the behavioral relationships between users, identities, and applications:
Behavioral Anomaly Detection monitors identity and access events across SaaS, flagging deviations from baseline behavior even when credentials appear valid
Session-Level Context and Correlation ties together login anomalies, MFA bypass patterns, and downstream application activity to identify real compromises early
Holistic Identity Telemetry provides visibility across SSO platforms and cloud applications—including lateral movement signals that siloed tools miss
Risk Scoring and Prioritization help the SOC quickly triage high-risk sessions for investigation before widespread damage occurs
By analyzing communication patterns and identity usage together, behavioral AI can identify signs that an account is being manipulated or used outside its normal operating profile—even when authentication appears valid.
Trust Is the New Attack Surface
The ShinyHunters campaign is a stark reminder that attackers don't always need bugs or zero-days to succeed. By weaponizing trust and identity flows that were designed for convenience, they're redefining what "secure" looks like in the cloud era.
As organizations lean further into SaaS and hybrid work, identity systems must evolve from gatekeepers into active defenders. That evolution demands identity contextualization, behavioral analytics, and solutions that connect the dots across users, accounts, and applications. Organizations that treat authentication as a final checkpoint rather than an ongoing risk signal will continue to face exposure.
The attacks attributed to ShinyHunters are unlikely to be the last to follow this model. But they provide a clear example of where the threat landscape is heading—and why identity-centric behavioral defense is becoming essential for protecting modern cloud environments.
For additional insight into the threat landscape, visit our threat intelligence data and research hub, Abnormal Intelligence.
Related Posts
Get the Latest Email Security Insights
Subscribe to our newsletter to receive updates on the latest attacks and new trends in the email threat landscape.